Insider Threat Prevention - To combat the insider threat, organizations should. Through a case study approach, this guide details an actionable framework for an effective insider threat mitigation program: The insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; This approach can help an organization define specific insider. Defining the threat, detecting and identifying. Organizations manage insider threats through. Threat detection and identification is the process by which persons who might present an insider threat risk due to their observable, concerning behaviors come to the attention of an. Proactively managing insider threats can stop the trajectory or change the course of events from a harmful outcome to an effective mitigation.
Defining the threat, detecting and identifying. To combat the insider threat, organizations should. Through a case study approach, this guide details an actionable framework for an effective insider threat mitigation program: Threat detection and identification is the process by which persons who might present an insider threat risk due to their observable, concerning behaviors come to the attention of an. Organizations manage insider threats through. Proactively managing insider threats can stop the trajectory or change the course of events from a harmful outcome to an effective mitigation. The insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; This approach can help an organization define specific insider.
Defining the threat, detecting and identifying. Through a case study approach, this guide details an actionable framework for an effective insider threat mitigation program: Threat detection and identification is the process by which persons who might present an insider threat risk due to their observable, concerning behaviors come to the attention of an. The insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; This approach can help an organization define specific insider. To combat the insider threat, organizations should. Organizations manage insider threats through. Proactively managing insider threats can stop the trajectory or change the course of events from a harmful outcome to an effective mitigation.
Insider Threat Prevention, Detection, Mitigation and Deterrence
The insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Defining the threat, detecting and identifying. Proactively managing insider threats can stop the trajectory or change the course of events from a harmful outcome to an effective mitigation. Threat detection and identification is the process by which persons who might present an insider.
Insider Threat Archives GRA Quantum
The insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Threat detection and identification is the process by which persons who might present an insider threat risk due to their observable, concerning behaviors come to the attention of an. To combat the insider threat, organizations should. Defining the threat, detecting and identifying. This.
Insider Threat Prevention Intelligent SecOps
Through a case study approach, this guide details an actionable framework for an effective insider threat mitigation program: The insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Threat detection and identification is the process by which persons who might present an insider threat risk due to their observable, concerning behaviors come to.
2023 Insider Threat Detection and Prevention Best Practices Sanity
Defining the threat, detecting and identifying. Threat detection and identification is the process by which persons who might present an insider threat risk due to their observable, concerning behaviors come to the attention of an. Proactively managing insider threats can stop the trajectory or change the course of events from a harmful outcome to an effective mitigation. To combat the.
An Ultimate Guide On Insider Threat Risks And Their Prevention AskPython
Threat detection and identification is the process by which persons who might present an insider threat risk due to their observable, concerning behaviors come to the attention of an. Proactively managing insider threats can stop the trajectory or change the course of events from a harmful outcome to an effective mitigation. This approach can help an organization define specific insider..
Insider Threat Report Crowd Research Partners
Defining the threat, detecting and identifying. The insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Through a case study approach, this guide details an actionable framework for an effective insider threat mitigation program: Threat detection and identification is the process by which persons who might present an insider threat risk due to.
Insider Threat Prevention Biometrica Systems, Inc.
Proactively managing insider threats can stop the trajectory or change the course of events from a harmful outcome to an effective mitigation. The insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Through a case study approach, this guide details an actionable framework for an effective insider threat mitigation program: Defining the threat,.
Strengthen Security by Addressing Insider Risk CloudOptics Multi
Organizations manage insider threats through. Threat detection and identification is the process by which persons who might present an insider threat risk due to their observable, concerning behaviors come to the attention of an. Defining the threat, detecting and identifying. Through a case study approach, this guide details an actionable framework for an effective insider threat mitigation program: The insider.
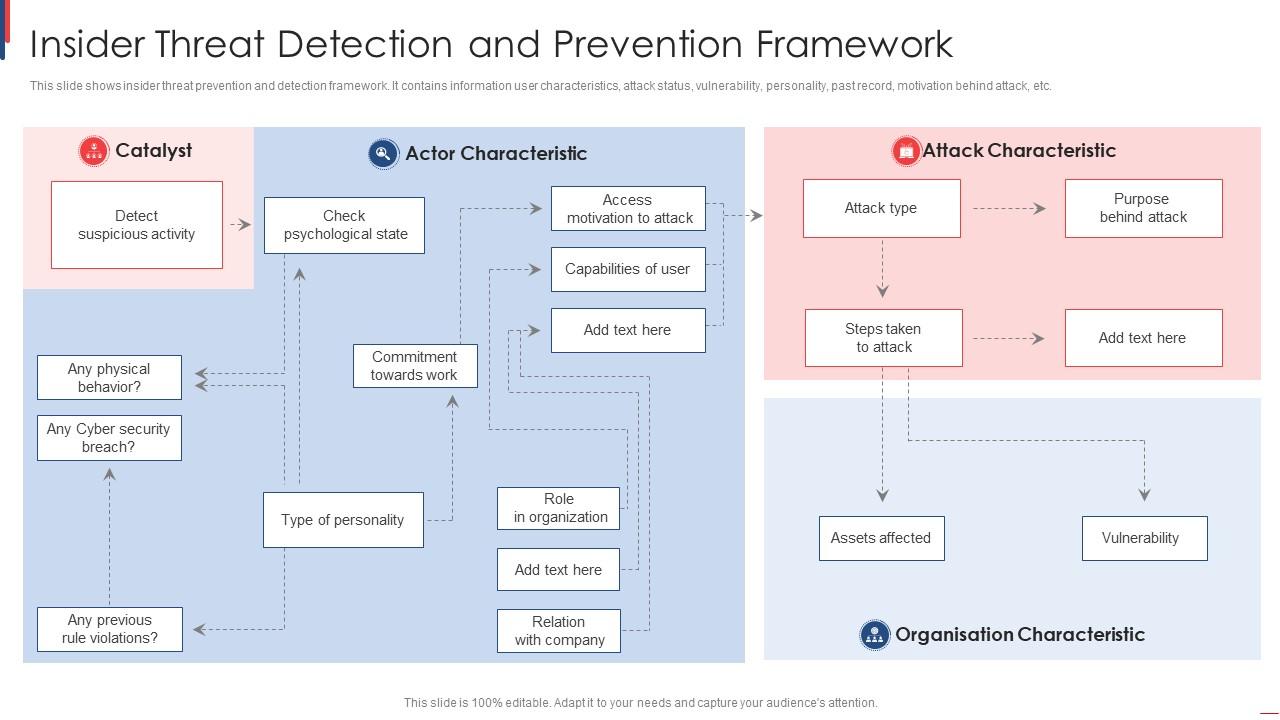
Insider Threat Detection And Prevention Framework PPT Presentation
This approach can help an organization define specific insider. To combat the insider threat, organizations should. Proactively managing insider threats can stop the trajectory or change the course of events from a harmful outcome to an effective mitigation. Through a case study approach, this guide details an actionable framework for an effective insider threat mitigation program: Defining the threat, detecting.
Insider Threats Risks, Identification and Prevention
The insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Threat detection and identification is the process by which persons who might present an insider threat risk due to their observable, concerning behaviors come to the attention of an. Defining the threat, detecting and identifying. Proactively managing insider threats can stop the trajectory.
This Approach Can Help An Organization Define Specific Insider.
To combat the insider threat, organizations should. Defining the threat, detecting and identifying. Threat detection and identification is the process by which persons who might present an insider threat risk due to their observable, concerning behaviors come to the attention of an. Organizations manage insider threats through.
Through A Case Study Approach, This Guide Details An Actionable Framework For An Effective Insider Threat Mitigation Program:
The insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Proactively managing insider threats can stop the trajectory or change the course of events from a harmful outcome to an effective mitigation.